About

Hello! I am Bruno P. Kinoshita or “kinow”, born and raised in Casa Verde, São Paulo, Brazil. A typical Paulistano. I moved to Tāmaki Makaurau Auckland, Aotearoa New Zealand, and lived there for 8 years. I currently live with my wife, Cibele, in Barcelona, Spain.
Head on to the blog for posts about languages, writing, music, arts, and computer programming. Or visit my portfolio where I upload drawings, illustrations, and paintings.
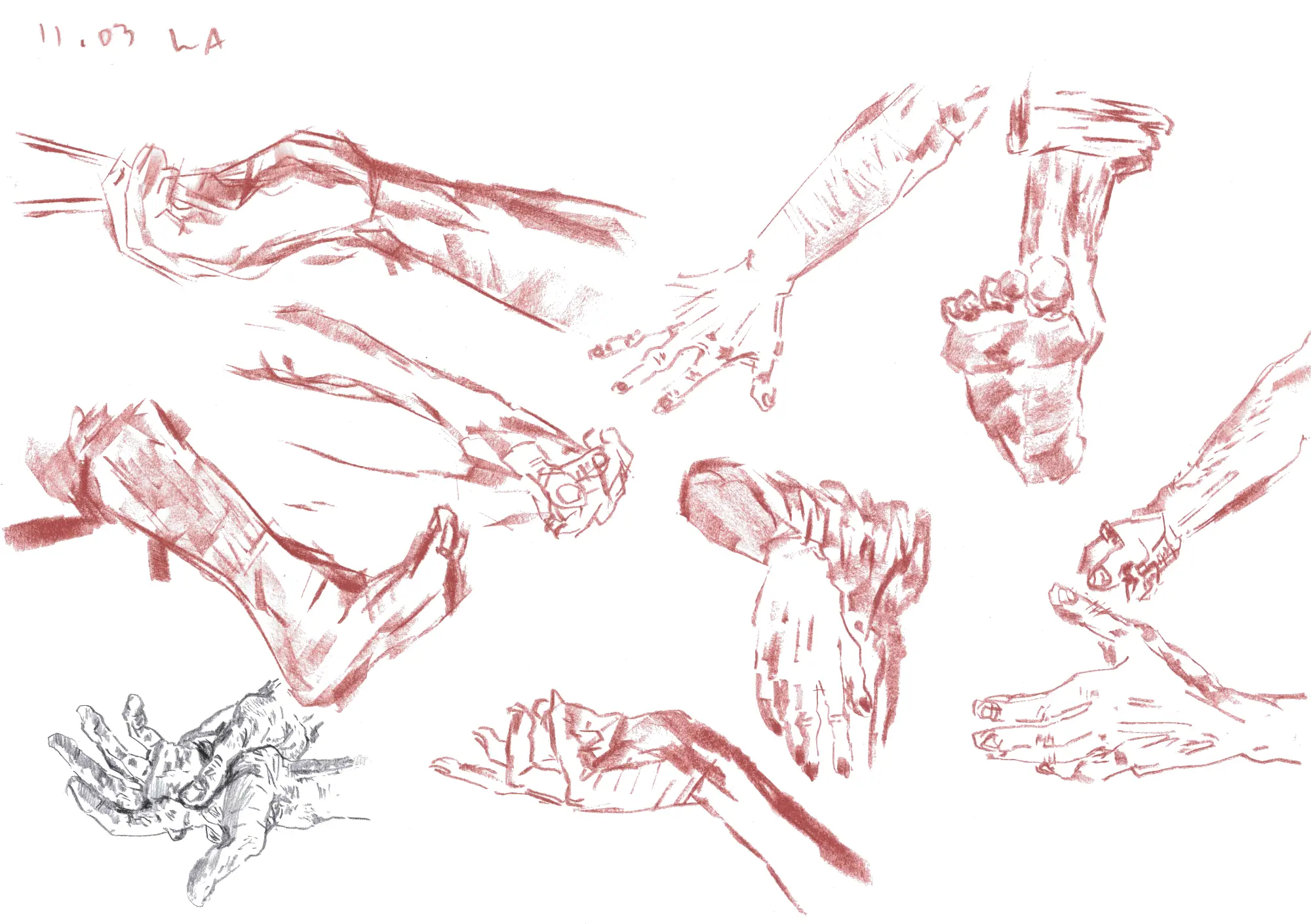
In arts, I enjoy life drawing, editorial illustration, gouache, watercolors, pastels, 3D, UI/UX, data visualization, and writing. Much of the way I draw and paint was imprinted on me by my late big brother, Joe Lauviah Morbitus Mortiferus (he would still want to be called that way, shrugs). I use mixed media, but tend to use more charcoal, graphite, and ink for traditional arts. For digital arts I use GIMP, Krita, Blender, ClipStudio Paint, and Inkscape.
In computer programming, I write code in Java, Python, JavaScript, PHP, and a few other languages. I am interested in natural language processing, languages (like Portuguese, Spanish, French, English, Catalan, Irish, Te Reo Māori, and Japanese), functional programming, linked data, reasoners, fuzzy logic, and all things open source. I have worked on Windows, Unix, Linux, Mainframe, HPC, and cloud. My father, Jorge Yoshio Kinoshita, had a career working with mainframes at IBM.

This website was created with Open Source software, following accessibility practices from the WCAG 2.1 standard, and in pure CSS without JavaScript. It does not use any cookies nor trackers. It was tested with the Orca screen reader on Ubuntu Linux. Feedback to improve accessibility is welcome.
Get in touch if you would like to discuss a project related to computer programming and, or, arts.
- Curriculum Vitae (PDF)
- ORCID